One key aspect of being able to secure your software ecosystem is to know what software you are using in the first place. Various tools and approaches are commonly used to analyze software after the fact, to attempt to determine what comprises a software distribution. However, a more useful approach can be to gather and record this information at the time the software is being built, when conclusions can be made with certainty about the software being used. This information can then be conveyed in a software bill of materials (SBOM) in a shared, standardized metadata format.
On August 18, the Linux Foundation hosted a virtual Supply Chain Town Hall where experts who have been working on how to solve these vulnerabilities for almost a decade, share insight and best practices on how to best protect your supply chain and mitigate potential disasters.
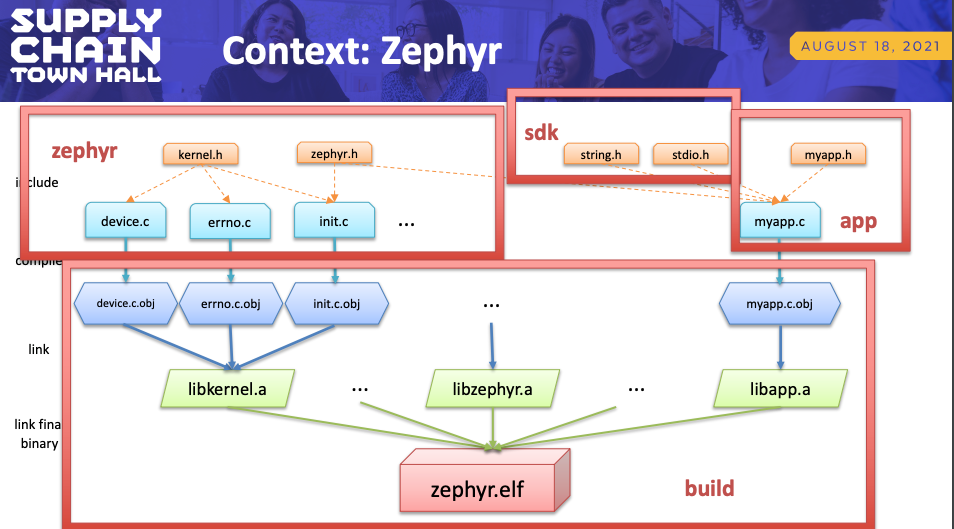
Steve Winslow, VP of Compliance & Legal, The Linux Foundation, discussed a recent addition to the build tooling for Zephyr, a C-language open source real-time embedded operating system. This added feature enables distributions of Zephyr to generate an SPDX SBOM for their particular configuration automatically at the time of build. He discusses how this functionality leverages existing aspects of the Zephyr build process to record data about which particular source files are compiled and linked into the final Zephyr binary that is installed on the embedded device. He also shares lessons learned and considerations for other projects that may want to take similar approaches.
If you missed the event, you can watch Steve’s presentation here: